- Jul 2
Protecting Against the Surge of Credential Stuffing Attacks
Updated: Jul 2

In the modern digital age, credential stuffing represents a severe security threat, where attackers leveraging stolen credentials compromise user accounts across multiple platforms. This form of attack highlights the critical need for advanced cybersecurity measures capable of thwarting such threats. A recent analysis by Okta has underscored the urgency of addressing these vulnerabilities with robust cybersecurity solutions.
AuthMind is at the forefront of combating these threats, with cutting-edge technology designed to detect and counteract the nuances of credential stuffing. This blog post will delve into how AuthMind’s Identity Security platform enhances organizational security by preemptively identifying and mitigating potential breaches.
Understanding Credential Stuffing
Credential stuffing is a prevalent cyberattack method where stolen account credentials, primarily usernames and passwords, are used to gain unauthorized access to user accounts across various platforms. This technique exploits the common and risky practice of password reuse—where individuals use the same password across multiple sites and applications.
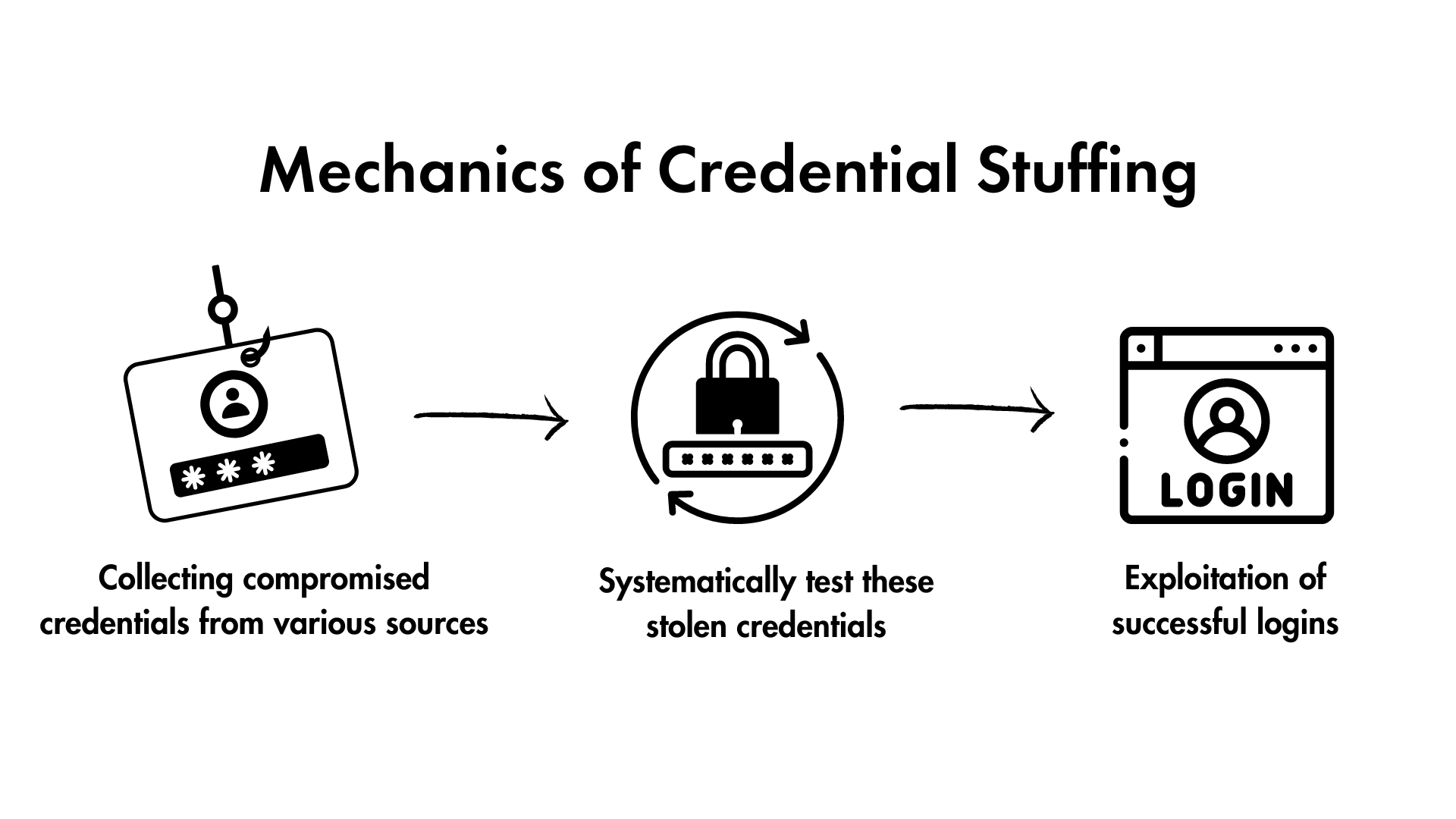
Mechanics of Credential Stuffing:
- Source of Credentials: The attackers usually start by collecting compromised credentials from various sources. These might include data breaches of popular services, phishing campaigns, or purchases on the dark web. Often, these credentials are compiled into large databases, which are then used in the attacks.
- Automated Login Attempts: With the help of automated scripts or bots, attackers systematically test these stolen credentials across numerous websites and applications. This process is typically rapid and can test thousands of login combinations across multiple sites within seconds.
- Exploitation of Successful Logins: When a match is found, and access is gained, attackers can exploit these accounts in several ways. They might steal sensitive personal information, hijack accounts for ransom, or use them to perpetrate further malicious activities such as spamming, phishing, or secondary fraud.
Case Study: The Norton LifeLock Incident
- The Incident: In a striking example of the dangers of credential stuffing, Norton LifeLock reported a massive breach involving approximately 925,000 user accounts. The attackers used credentials previously exposed in unrelated breaches to gain unauthorized access to these accounts.
- Consequences: This attack not only compromised personal and financial information of nearly a million individuals but also severely damaged Norton LifeLock’s reputation. The incident highlighted the significant financial and operational impacts of credential stuffing, with Norton facing potential financial repercussions both from direct losses and from increased scrutiny and regulation.
- Response and Resolution: Following the breach, Norton LifeLock had to undertake extensive remedial measures. These included forced password resets, increased security measures, and comprehensive audits to ensure no further vulnerabilities were present. The company also had to manage the public relations fallout, reassuring customers and stakeholders about the safety of their platforms.
Broader Implications
- For Businesses: Credential stuffing poses a grave threat to businesses of all sizes, jeopardizing sensitive business information, intellectual property as well as customer trust, and potentially leading to substantial financial and reputational damage.
- For Individuals: Users are at risk of identity theft, financial fraud, and loss of personal data, which can have long-lasting repercussions on their personal and professional lives.
Credential stuffing attacks are particularly effective because they are simple to execute, hard to detect, and can be highly damaging. They exploit a critical vulnerability in online security practices—password reuse. This breach at Norton LifeLock serves as a vivid reminder of the need for stronger security practices both at the individual and organizational levels, such as implementing robust, unique passwords for each site and service and using multi-factor authentication (MFA) wherever possible.
AuthMind addresses these weaknesses proactively, and help defend against attacks through advanced detection and response mechanisms, providing businesses with the tools they need to protect against credential stuffing effectively.
AuthMind: Bolstering Defenses Against Credentail Stuffing
AuthMind equips organizations with a sophisticated and multi-faceted defense mechanism against credential stuffing attacks, utilizing cutting-edge Identity Threat Detection and Response (ITDR) and Identity Security Posture Management (ISPM). These systems work collaboratively to not only detect and respond to threats but also to proactively enhance the organization's overall security posture. Here’s an in-depth look at how each component contributes to safeguarding businesses:
Identity Threat Detection and Response (ITDR)
Real-Time Threat Identification:
AuthMind's ITDR capabilities continuously monitors and analyzes data across the environment to detect abnormal activities that suggest potential credential stuffing attempts. By leveraging real-time analytics, AuthMind identifies unusual patterns such as rapid spikes in login failures, access requests from geographically inconsistent locations, or simultaneous logins from disparate devices, all indicative of credential stuffing.
Automated Incident Response:
Upon detection of a potential threat, AuthMind's ITDR system can initiate automated response protocols. These responses are tailored to the nature of the threat and the specific policies of the organization.
Example: Imagine a situation where multiple failed login attempts are detected from foreign IP addresses on high-value corporate executive accounts. AuthMind’s ITDR system would instantly flag this activity, notify the security team, and can prompt immediate changes to apply conditional access policies to block the offending IPs, effectively thwarting the attack before any data breach could occur.
Identity Security Posture Management (ISPM)
Continuous Security Assessments:
AuthMind's ISPM capabilities involve continuous assessment of an organization’s identity management and security practices. This includes checking for adequate MFA protection, ensuring proper activity of identities and identity systems, and identifying risky user behaviors.
Enhancing Identity Configurations:
By regularly monitoring the identities, identity systems activity and practices, AuthMind helps organizations identify and rectify potential vulnerabilities. This proactive approach not only prevents credential stuffing attacks but also strengthens the security of all identity-related interactions within the system.
Example: At a company using multiple SaaS products, AuthMind could identify and alert the IT department about services that lack adequate MFA protection or aren’t managed by an IDP. Following this, it could guide the IT team through the process of enforcing stronger authentication protocols, significantly reducing the risk of credential theft and stuffing.
Complete Observability into ALL Identity Activity with AuthMind
AuthMind’s continuous observability into Identity activity is a cornerstone in the defense against credential stuffing, employing advanced identity activity analysis, enriched data contextualization, and proactive alert systems to detect and respond to threats dynamically.
Identity Activity Analysis
Monitoring Flow Activity:
AuthMind leverages extensive identity activity data, utilizing technologies like SIEM solutions to monitor flow activity across the environment. This monitoring is critical in identifying abnormal patterns that may signify an attack, such as spikes in traffic to authentication systems or unusual access requests to critical resources.
- Early Threat Indicators: By analyzing identity activity, AuthMind is able to detect early indicators of credential stuffing attacks, such as unusual volumes of login attempts or traffic from known malicious IP addresses. This early detection is key to preventing potential breaches before they escalate.
Contextual Enrichment of Access Flow Activity:
Each access flow activity is enriched with additional context to provide a clearer picture of its source and intent.
- Enhanced Data Contextualization: This involves correlating each IP address with user/service identities, device information, and geographical locations, transforming raw data into actionable intelligence that triangulates the attacker even if they are faking hostnames or IPs. This allows Authmind to create a full path of the access flow, e.g. through VPN, ZTNA, etc. For example, if a login attempt comes from a geographical location that does not match the user’s typical pattern, AuthMind can flag this as suspicious.
- Distinguishing Between Threats and Legitimate Activities: The enriched access flow activity helps AuthMind accurately differentiate between legitimate user activities and potential security threats, thereby reducing false positives and focusing security efforts where they are needed most.
Identity and Access Context
MFA and Authentication Monitoring:
Beyond simple monitoring, AuthMind analyzes authentication attempts throughout the network, ensuring that Multi-Factor Authentication (MFA) protocols are followed and identifying any deviations that might indicate a security breach.
- Policy Compliance Checks: AuthMind continuously verifies that MFA settings align with organizational policies, providing an additional layer of security by ensuring that all access points are protected according to predefined standards.
- Detection of Bypassed MFA Protections: In instances where MFA protections are bypassed, either through configuration errors or deliberate actions by attackers, AuthMind quickly identifies these vulnerabilities. By monitoring how and when MFA protocols are circumvented, AuthMind can alert the security team to potential credential stuffing or other forms of identity-based attacks.
- Example Scenario: If an employee's credentials are used from a location or device not previously associated with them, and the login does not prompt for MFA as expected, AuthMind would flag this anomaly. The security team would be alerted immediately, allowing them to take swift action, such as forcing a logout and requiring a password change and re-authentication with MFA.
Proactive Alerting System
Automated Alerts:
AuthMind's alert system employs advanced algorithms to analyze insights from network flow analysis and identity context assessments. This sophisticated alert system proactively notifies the security team of any suspicious activities detected across the network. Alerts are prioritized based on several critical factors:
- Threat Potential: Alerts are classified according to the potential impact and threat likelihood, ensuring that the most serious threats are escalated to the top of the priority list.
- Customizable Thresholds: Organizations can set specific thresholds for different types of alerts, allowing for tailored responses based on the sensitivity and security requirements of different areas of the business.
Real-Time Notifications:
When a potential threat is identified, AuthMind generates real-time notifications that provide security teams with comprehensive details about the incident:
- Incident Details: Each alert includes a detailed description of the suspicious activity, such as unusual login patterns, geolocation anomalies, or deviations from normal access routines.
- Recommended Actions: To facilitate immediate action, alerts propose recommended steps to mitigate the risk, such as enforcing additional authentication checks, temporarily disabling affected accounts, or conducting immediate investigations.
- Direct Links: Notifications include direct links to the affected accounts or systems, allowing security personnel to quickly access and address the issue, potentially stopping credential stuffing attacks in their tracks.
Integrated Response Options:
AuthMind integrates directly with other security systems, enabling automated responses or manual intervention from within the platform. This integration helps streamline the process of addressing alerts, reducing response times and enhancing the effectiveness of security measures.
SaaS and Cloud Access Flow Activity Observability
Extended Flow Activity Observability Capabilities:
Understanding that modern enterprises operate across multiple cloud and SaaS platforms, AuthMind extends its identity observability capabilities to these environments. This is crucial for providing a holistic security posture that covers all potential entry points used in credential stuffing attacks.
- Comprehensive Coverage: AuthMind monitors activities across all connected SaaS and cloud services, including popular platforms like AWS, Google Cloud, Microsoft Azure, and various SaaS applications. This ensures that no part of the organization’s digital footprint is left unprotected.
- Cloud-Specific Insights: The system tailors its monitoring to the specific characteristics of each platform, recognizing the unique security configurations and potential vulnerabilities of different cloud services.
Anomaly Detection in Cloud Environments:
AuthMind’s monitoring tools are equipped to detect anomalies specifically in cloud and SaaS environments, which might include:
- Unusual Access Patterns: Such as accessing cloud storage or SaaS applications from new devices or locations that do not match the historical pattern.
- API Anomalies: Suspicious activities related to API usage, which are often overlooked but can provide a gateway for attackers to manipulate cloud resources.
Discovery of Unknown Assets and Users
Detecting Shadow IT: AuthMind's advanced identity observability capabilities extend beyond traditional asset discovery, uncovering unknown identity systems and shadow IT that are often hidden within an organization’s network. These systems can range from unauthorized cloud services and SaaS applications to unofficial software installations that bypass standard IT protocols.
- Comprehensive Visibility: AuthMind uses a combination of network traffic analysis, machine learning, and pattern recognition to detect anomalies that may signify the use of unauthorized applications or services. This approach helps in mapping all digital assets, providing a complete inventory that includes often-overlooked shadow IT.
- Risk Assessment and Management: By identifying these blind spots, AuthMind allows organizations to either integrate these systems into their official IT environment securely or remove them to mitigate potential security risks. This proactive measure significantly enhances the security posture by closing gaps that could be exploited by attackers.
Identifying Shadow Assets and Who Is Accessing Them:
AuthMind’s capabilities also extend to detecting and managing shadow users—individuals using IT resources without proper authorization—and unmanaged devices that connect to the environment.
- User and Device Profiling: AuthMind profiles each user and device accessing the network to create a baseline of normal activity patterns. Any deviation from this baseline, such as a new device accessing sensitive data or a user executing unusual commands, triggers an investigation.
- Enhanced Endpoint Security: For devices, AuthMind ensures that all endpoints are compliant with security policies, regardless of whether they are formally managed by IT. This includes mobile devices, IoT devices, and personal laptops used in a BYOD (Bring Your Own Device) policy context.
Real-Time Alerting and Response
Automated Alerts: AuthMind’s alert system utilizes the rich data collected and analyzed to proactively notify security teams about potential threats. These automated alerts are generated in real time, ensuring that security teams can react promptly to potential incidents of credential stuffing or other security breaches.
- Detailed Threat Intelligence: Alerts provide comprehensive details about the nature of the threat, including the specific assets, users, or systems involved. This information helps in assessing the severity and potential impact of the threat.
- Prioritization of Alerts: Alerts are prioritized based on the severity and immediacy of the threat, allowing security teams to focus their efforts where they are most needed. This prioritization is critical during high-volume attack scenarios, ensuring that the most dangerous threats are addressed first.
Actionable Insights for Rapid Response:
Each alert not only notifies but also provides actionable insights designed to facilitate immediate and effective response measures.
- Guided Responses: For instance, if a potential credential stuffing attack is detected, the alert will include recommended actions such as immediate account lockout, password resets, or MFA challenges. These steps can be initiated directly from the alert interface, speeding up the response time.
- Integration with Incident Response Platforms: AuthMind’s alerts can be integrated with existing incident response platforms, allowing automated or semi-automated responses based on predefined protocols. This integration streamlines the process, reducing the time from detection to resolution.
Conclusion
AuthMind's approach to complete observability and protection of identity access transcends traditional monitoring techniques. It is a proactive, informed, and richly contextualized defense mechanism specifically designed to combat credential stuffing attacks—one of the most pervasive threats in today's digital landscape. Through advanced network flow analysis, enriched IP data contextualization, and the strategic detection of unrecognized assets and users, AuthMind equips organizations not only to detect but also to respond effectively to sophisticated cyber threats.
By integrating deep network insights with comprehensive identity monitoring, AuthMind creates a robust defense against unauthorized access attempts, ensuring that all aspects of an organization’s IT environment are secure. This proactive and dynamic approach helps safeguard sensitive data and maintain operational integrity, even as threat landscapes evolve and become increasingly complex.
Call to Action
As credential stuffing attacks continue to rise, the need for advanced security solutions becomes ever more critical. AuthMind stands at the forefront of this technological battle, offering cutting-edge defenses that are vital for any organization serious about protecting its digital assets. Don't wait for a security breach to reveal the vulnerabilities in your system—take action today.
Discover how AuthMind can fortify your cybersecurity posture, enhance your threat detection capabilities, and ensure you stay one step ahead of cybercriminals. Contact us now to schedule a demonstration or to speak with one of our cybersecurity experts about how AuthMind can be tailored to meet your specific security needs.

